The Ultimate Directory for Offensive Security
A database for red teaming, penetration testing, and ethical hacking resources

Moxy is an open-source DAST tool with agentic AI for modern web application security testing and automated pentesting workflows.
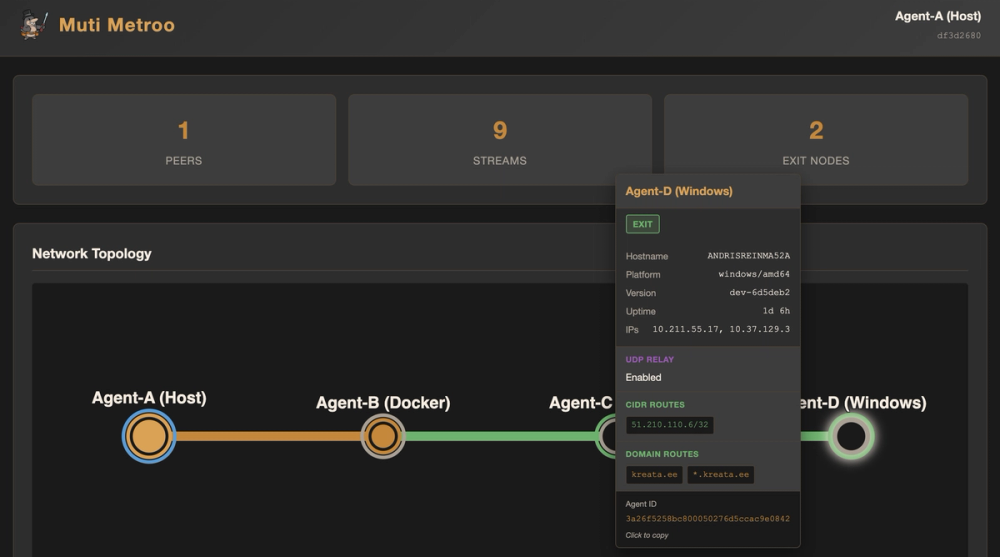
A userspace mesh networking agent that creates virtual TCP tunnels across heterogeneous transport layers. Multi-hop routing with SOCKS5 ingress, CIDR-based exit routing, and end-to-end encryption (X25519 + ChaCha20-Poly1305). No root required.

Nessus Essentials is a free vulnerability scanner by Tenable, offering high-speed, in-depth scanning for up to 16 IP addresses.

NetExec is a network service exploitation tool designed to automate security assessments of large networks.