A database for red teaming, penetration testing, and ethical hacking resources
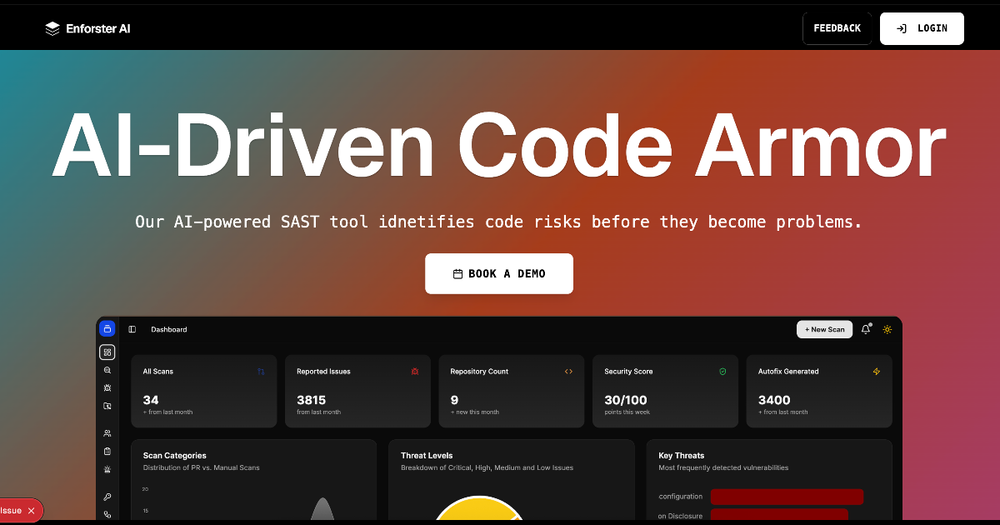
AI-native SAST tool for code security, detecting vulnerabilities, secrets, IaC issues, and AI model security with actionable AI fixes.

Evil Crow RF V2: A radio frequency hacking device for pentesting and red team ops, operating across multiple bands with dual CC1101 modules.