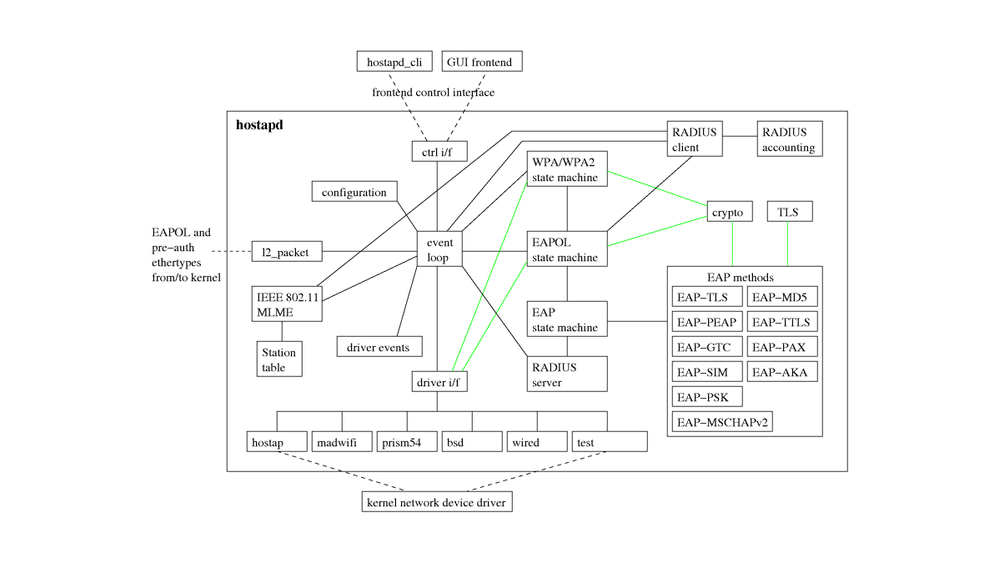
hostapd-wpe (Wireless Pwnage Edition)
hostapd-wpe is a modified version of hostapd designed to facilitate AP impersonation attacks. It's a replacement for FreeRADIUS-WPE, implementing IEEE 802.1x Authenticator and Authentication Server impersonation attacks to obtain client credentials and establish connectivity.
Key Features:
- EAP Impersonation: Supports various EAP types for impersonation, including EAP-FAST/MSCHAPv2, PEAP/MSCHAPv2, EAP-TTLS/MSCHAPv2, EAP-TTLS/MSCHAP, EAP-TTLS/CHAP, and EAP-TTLS/PAP.
- Credential Harvesting: Returns an EAP-Success message to the client after credentials are harvested, making the client believe they are connected to a legitimate authenticator.
- Karma-Style Probes: Implements gratuitous probe responses for 802.11 clients, inspired by JoMo-Kun's patch.
- Heartbleed Attack: Implements CVE-2014-0160 (Heartbleed) attacks against vulnerable clients, inspired by the Cupid PoC.
- Logging: Logs all data to stdout and
hostapd-wpe.log.
Use Cases:
- Penetration testing of wireless networks.
- Auditing the security of EAP-based authentication.
- Demonstrating the risks of AP impersonation attacks.
- Testing client-side vulnerability to Heartbleed.
Target Users:
- Security researchers
- Penetration testers
- Network administrators
- Ethical hackers