Curated databases, exploit indexes, and analytical resources for tracking and understanding vulnerabilities. Includes CVE feeds, proof-of-concept repositories, prioritization tools, and in-depth writeups from the security community.

Vulnetic AI is a high-performance hacking agent built for serious penetration testing at a fraction of typical costs.

Aikido is a security platform for code and cloud, designed to automatically find and fix vulnerabilities in one central system.
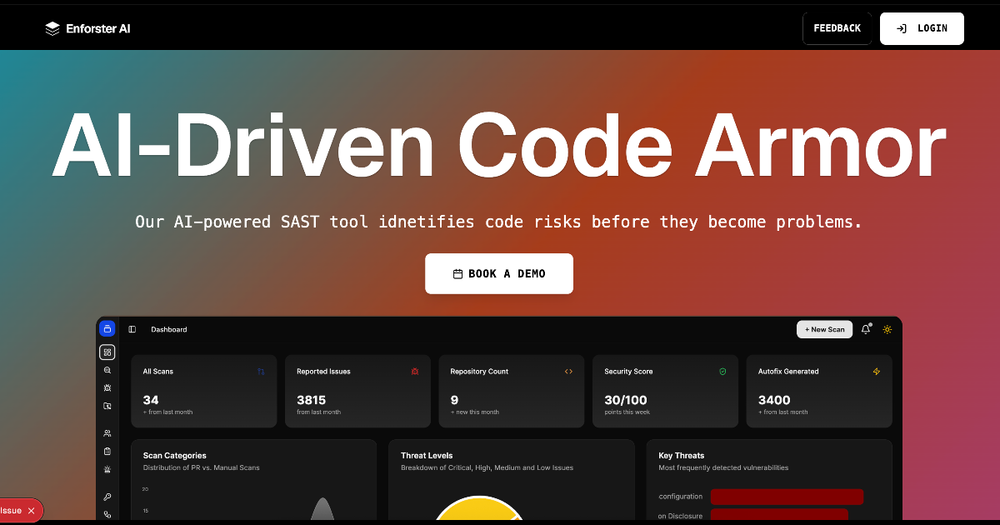
AI-native SAST tool for code security, detecting vulnerabilities, secrets, IaC issues, and AI model security with actionable AI fixes.